KB: 1080
Configuring Tamper Rules to Prevent Man-in-the-Browser (MITB) Attacks
This document explains how to configure Tamper Rules in the WAF to protect application parameters from client-side manipulation and thereby mitigate Man-in-the-Browser (MITB) attacks.
Problem Statement
Web applications that process sensitive user input, such as authentication parameters, are vulnerable to Man-in-the-Browser (MITB) attacks when client-side request integrity is not enforced. In a MITB scenario, malicious scripts or malware running within the user’s browser can intercept, manipulate, or inject values into HTTP requests before they are sent to the server.
Critical parameters—such as usernames, session identifiers, or transaction data—can be silently altered at the browser level, making the attack difficult to detect using traditional transport-layer security alone. To address this risk, the WAF must enforce parameter protection and attribute validation to ensure that request data has not been manipulated at the client side. By validating both the parameter name and its value across all URIs and HTTP methods, unauthorized modifications or abnormal injections—commonly associated with MITB activity—can be detected and blocked, preserving request integrity and preventing unauthorized access.
Solution
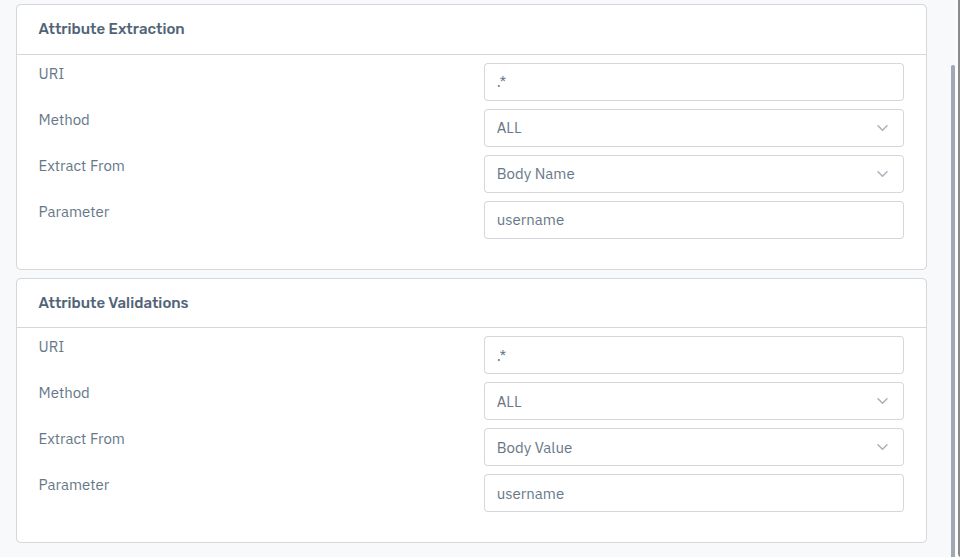
1. Configure Tamper Rules
Navigate to Tamper Rules in the WAF.
Refer to the documentation to understand the configuration in detail: Tamper Rules Configuration Guide
Configure the rule as shown below:
2. Configure Encryption / Secret Key
Ensure that a secret encryption key is configured to strengthen client-side protection and prevent browser-level parameter manipulation.
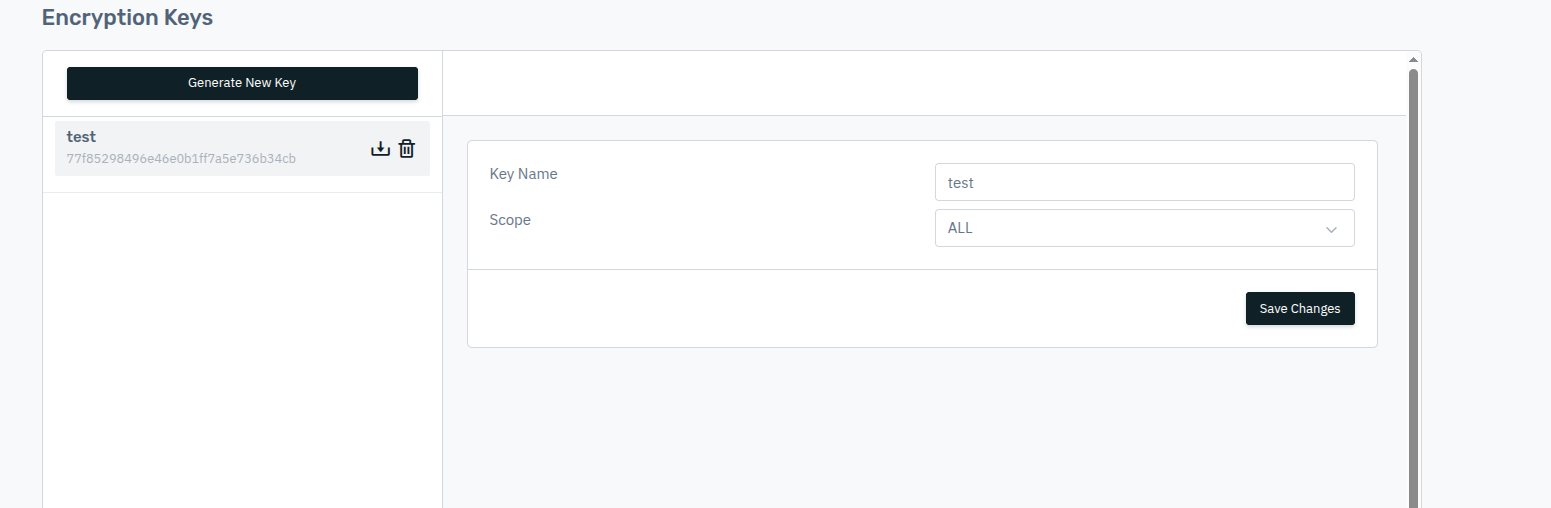
3. Update Security Settings
Add the previously created encryption key under the Security Settings section and enable client-side protection to ensure parameter integrity from the browser to the server.

Observation
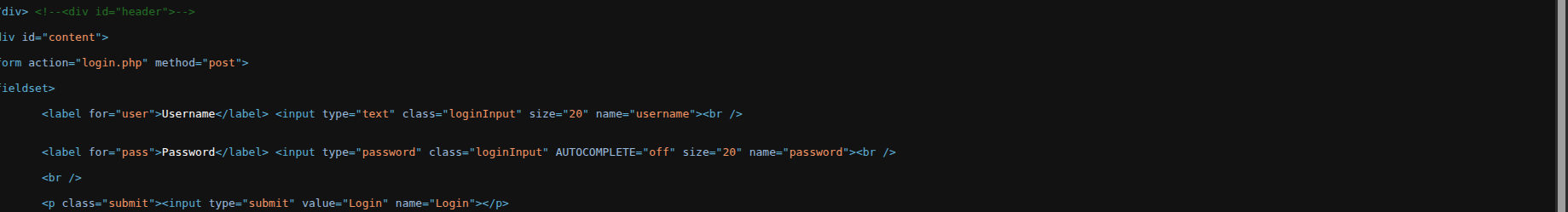
Before Configuration
Before applying the tamper rule configuration, application request parameters are transmitted in a predictable form, allowing malicious browser-based scripts to intercept and manipulate values prior to submission.
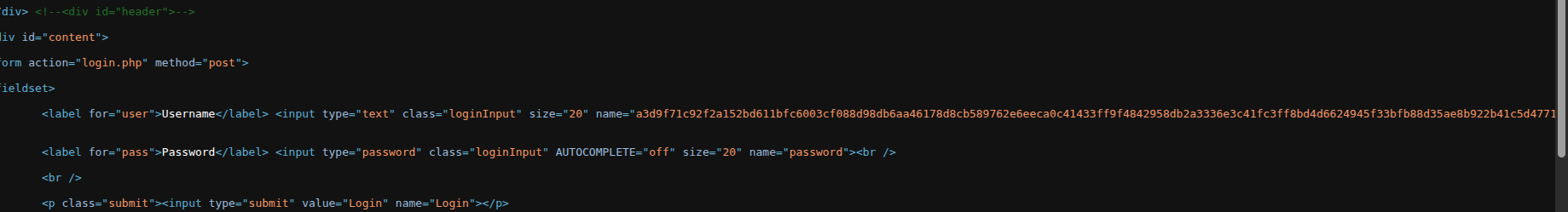
After Configuration
After configuring the tamper rule and enabling client-side security, sensitive parameters are protected and appear in a secured or encoded form, preventing browser-level manipulation before the request reaches the server.
Conclusion
By implementing Tamper Rules in combination with encryption and client-side security settings, the WAF effectively mitigates Man-in-the-Browser (MITB) attacks. This approach ensures parameter integrity, detects unauthorized browser-level modifications, and blocks malicious requests before they are processed by the application.
Summary
- Prevents client-side parameter manipulation
- Mitigates Man-in-the-Browser (MITB) attack risks
- Enforces strict attribute extraction and validation
- Strengthens security using encryption keys
- Preserves request integrity from browser to server across all URIs and HTTP methods