KB: 1070
How to decrypt SSL/TLS traffic using Wireshark and private keys?
Resources
Download the packet capture (.pcap)
Pre-Requisites
- Wireshark software
- Private Key: You need the private key of the server used in the SSL/TLS connection. This method only works for protocols like HTTPs where you have access to the private key.
- The RSA private key file is in PEM format.
Note
Wireshark primarily supports RSA private keys for decrypting SSL/TLS traffic. However,You cannot decrypt Diffie-Hellman Ephemeral (DHE) key exchanges. Therefore, traffic using these ciphers will not be decoded.
For more information regarding SSL/TLS DECRYPTION please refer to KB: 1077 SSL/TLS DECRYPTION
Steps
-
Load the Captured File
- Open Wireshark and load your .pacp
-
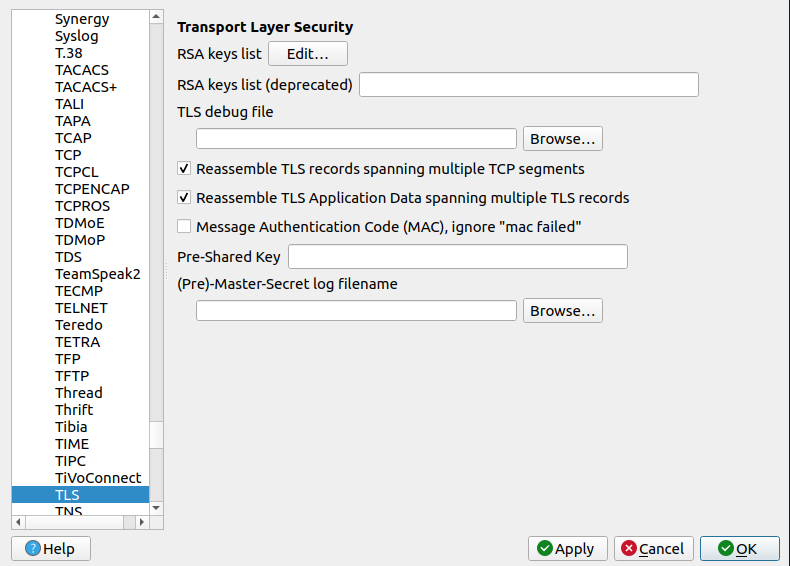
Configure the SSL/TLS Preferences
- Go to Edit > Preferences
- Expand the protocols list on the left side.
- Scroll down and select TLS or SSL (depending on your Wireshark version)
-
Add the Private key
-
In the same preferences window under TLS or SSL, find the RSA keys list.
-
Click on the Edit button
-
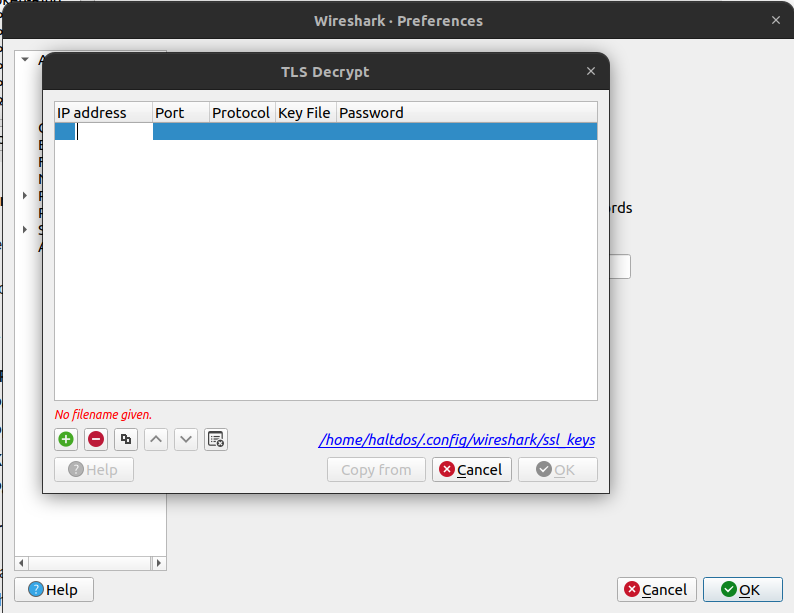
Add a new entry with the following details:
- IP address: The IP adress of the server.
- Port: The port number(e.g, 443 for HTTPS)
- Protocol: Typically, HTTP
- Key File: Browse and select the server's private key file
- Password: If the key file is encrypted, enter the password.
-
-
View Decrypted Data
- Wireshark should now automatically decrypt the SSL/TLS traffic using the private key.
- You can inspect the decrypted packets, including HTTP requests and responses, directly in Wireshark .