KB: 1073
Primary troubleshooting steps for issues found in applications onboarded on Haltdos WAF
When troubleshooting issues with applications onboarded on Haltdos WAF, use a systematic approach to identify and resolve the root cause. For instance, users will see a reference ID on the screen when Haltdos WAF blocks a request, which can be used to check incident details, including status code, URI, and source IP and much more information about the incident, under Apps > WAF > Incidents.
Below are some common cases-
-
Internal Server Error (5xx)
a. Cause: This error often indicates a problem with the backend server of the application or an issue with how the WAF is interacting with the backend server.
b. Troubleshooting steps:
-
Inspect WAF Logs: Analyze the Incidents logs to see if any security rules were triggered that might have affected the request.
A misconfiguration in the server configuration, including the server IP or port configured in Server Group, could cause a server error. -
Try to connect to the Backend Server: You can check if the WAF Mitigation Instance can connect to the backend server and verify the response using telnet and curl request through CLI.
Example-
telnet example.com 80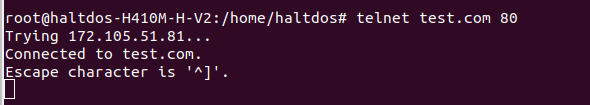
curl --resolve example.com:443:93.184.216.34 https://example.com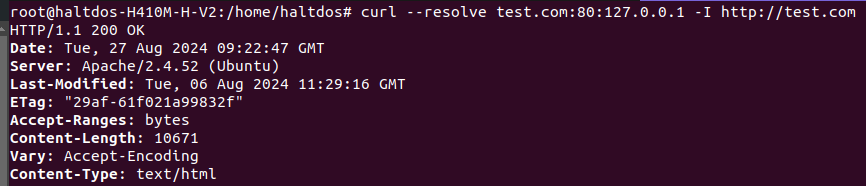
-
Check Application Logs: After reviewing Incident Logs review the application's server logs to identify any server-side errors or exceptions that could have triggered the 500 error.
-
Review Configuration: User can disable error handling to get the exact response from backend server.
-
-
Gateway Timeout (504)
-
Cause: This error often indicates a problem with the backend server of the application or an issue with the WAF, where it is unable to receive a response from the backend within the configured connection timeout period.
-
Troubleshooting steps:
-
Inspect WAF Logs: Analyze the Incidents logs to see if WAF is getting response from the Backend Server.
-
Change the configured time period to get the response You can try to increase the Connection Timeout and again try to send the request.
-
Check Application Logs: Review the application’s server logs to identify any server-side errors or exceptions that could have triggered the 504 error.
-
-
-
Forbidden Error (403)
-
Cause: The HTTP 403 Forbidden error response status code indicates that the Haltdos WAF understood the request but refused to process it. This could be due to the request being malicious or the WAF consider it as malicious (a false positive).
-
Troubleshooting steps:
- Inspect WAF Logs: Analyze the Incidents logs to see if any security rules were triggered that might have affected the request. There, you can identify the actual reason for the blocked request, and the user can take the necessary steps to whitelist the incident that occurred if needed.
-
-
Page Not Found (404)
-
Cause: The HTTP 404 Not Found error response status code indicates that the server cannot find the requested resource, or the links are broken.
-
Troubleshooting steps:
-
Check requested URL: Ensure the URL is typed correctly. Some URLs require a trailing slash (/) at the end, missing it can lead to a 404 error.
-
Check Application Logs: Review the application's server logs to identify any server-side errors or exceptions that could have triggered the 404 error.
-
-
-
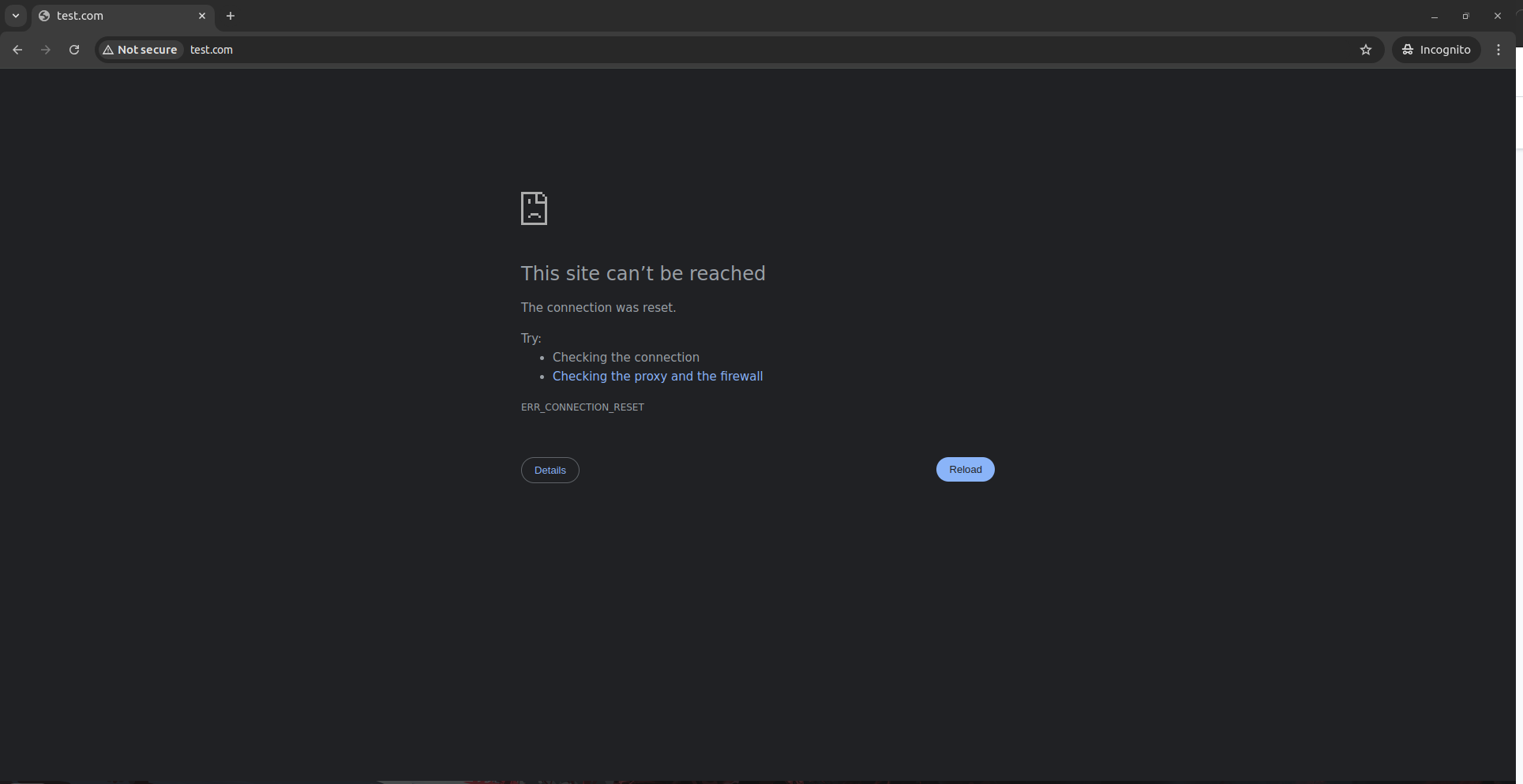
No Response (444)
- Description: If any policies have been configured on Haltdos WAF for Geo Filtering, such as IP Blacklist or Country Blacklist, users may see a "Site Can't Be Reached" message or something similar. Incident information related to these events can be viewed on the Haltdos Console under Incidents.
-
Cause: The HTTP 444 status code typically indicates that the WAF has returned no response to the client and closed the connection.
-
Troubleshooting steps:
-
Inspect WAF Logs: Analyze the Incident logs to see why the request has been blocked.
-
Review Configuration: User can review the geo filtering policies to see if anything is misconfigured.
-