KB: 1078
How to configure the capture rule to analyze the HTTPS traffic ?
Problem statement
How can HTTPS traffic be selectively decrypted for analysis by securely logging SSL/TLS session keys based on configurable criteria using capture rule?
Solution
The WAF can log SSL/TLS session keys based on configurable criteria defined in the capture rule to generate the SSLKEYLOG file and .pcap file, which will provide detailed information about the network activity over Wireshark.
Steps to Solve:-
- Login into Haltdos console.
- Go to Apps > WAF > Listener > go to listener.
- In the selected Listener > SSL Management > check for ssl certificate configuration > Save Changes.
- Now go to Rules > Capture Rule.
- Now configure the Capture Rule based on the required specification.
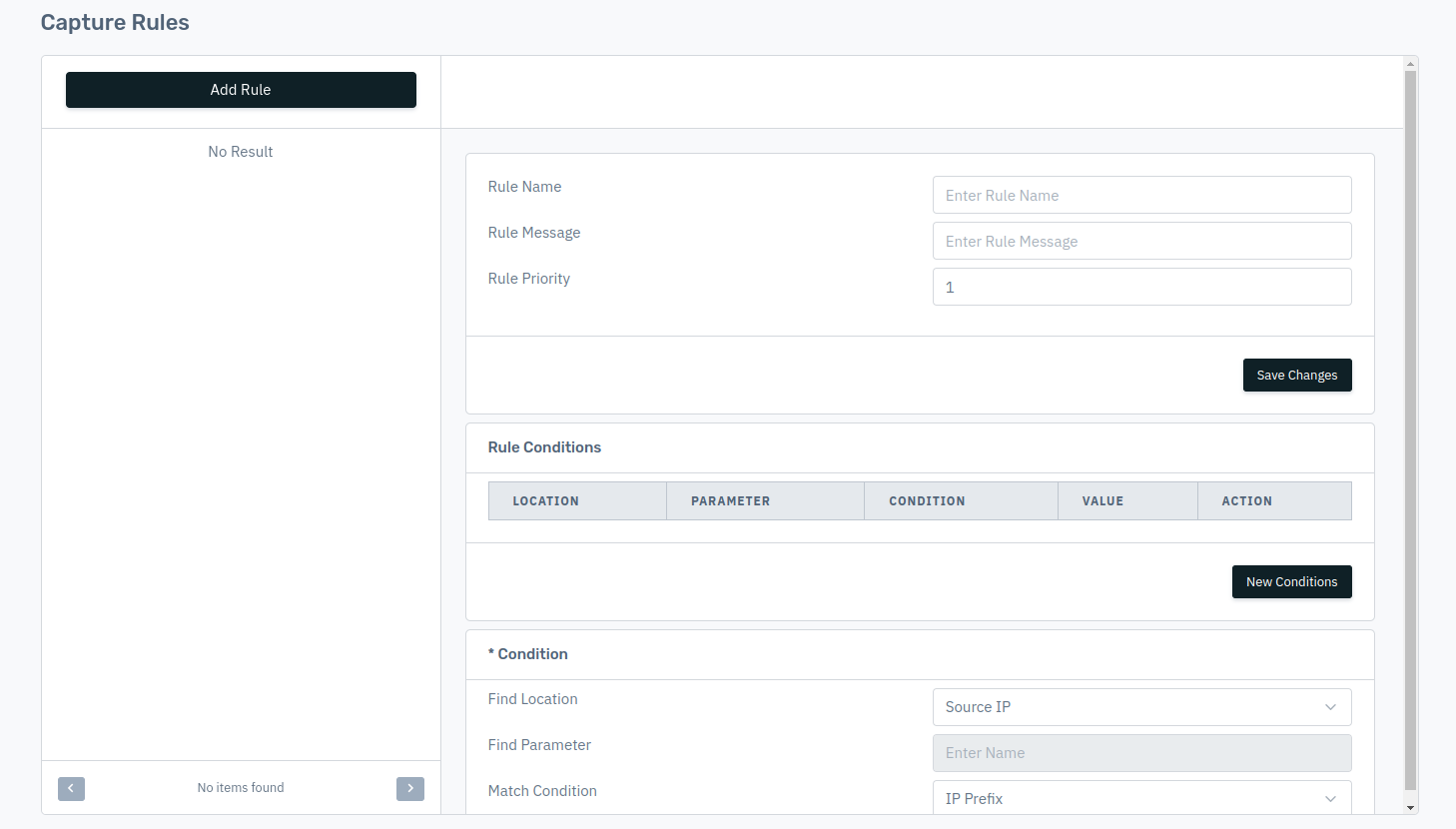
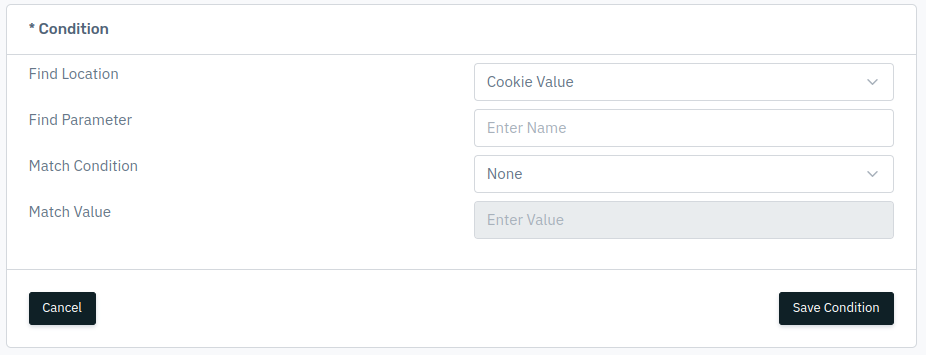
- In the conditions section, users can select their required criteria, such as:
- Find Location: It includes various conditions such as client Browser, OS, Device, Source IP etc.
- Find Parameter: Enter the parameter for the location.
- Match Condition: It includes pattern exists, pattern don't exists, equals or not equals etc.
- Match Value: Enter the value for the match condition.
After configuring the capture rule, it will generate the SSLKEYLOG file in the path file: /var/log/haltdos/offloader.
Genrating the .pcap file
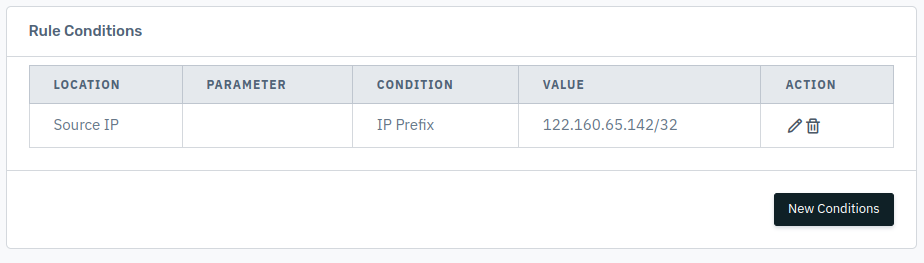
Step 1 - If you want to apply the capture rule to a specific client machine or server, enter its IP address in the condition section of the capture rule and save condition.
Step 2 - Open that listener using HTTPS in a browser tab and let it receive some traffic.
Step 3 - Now, on the WAF server where the listener is deployed, run the following command:
tcpdump -i any port 443 and host <hostname> -w dump.pcap
Step 4 - This will capture the traffic that has been received from the client machine or server IP configured in the capture rule.
Step 5 - Now, after stopping the tcpdump command, the user will have the dump.pcap file.
With the capture rule in place, the next step is to decrypt the recorded SSL/TLS traffic using Wireshark.
Requirements
-
Captured .pcap file from your network traffic.
-
The SSL session key log file or server private key.
-
Wireshark installed.
-
Get the key log file generated by Haltdos WAF from the capture rule.
-
In Wireshark, go to Edit > Preferences > Protocols > TLS.
-
Under (Pre)-Master-Secret log filename, enter the path to the key log file.