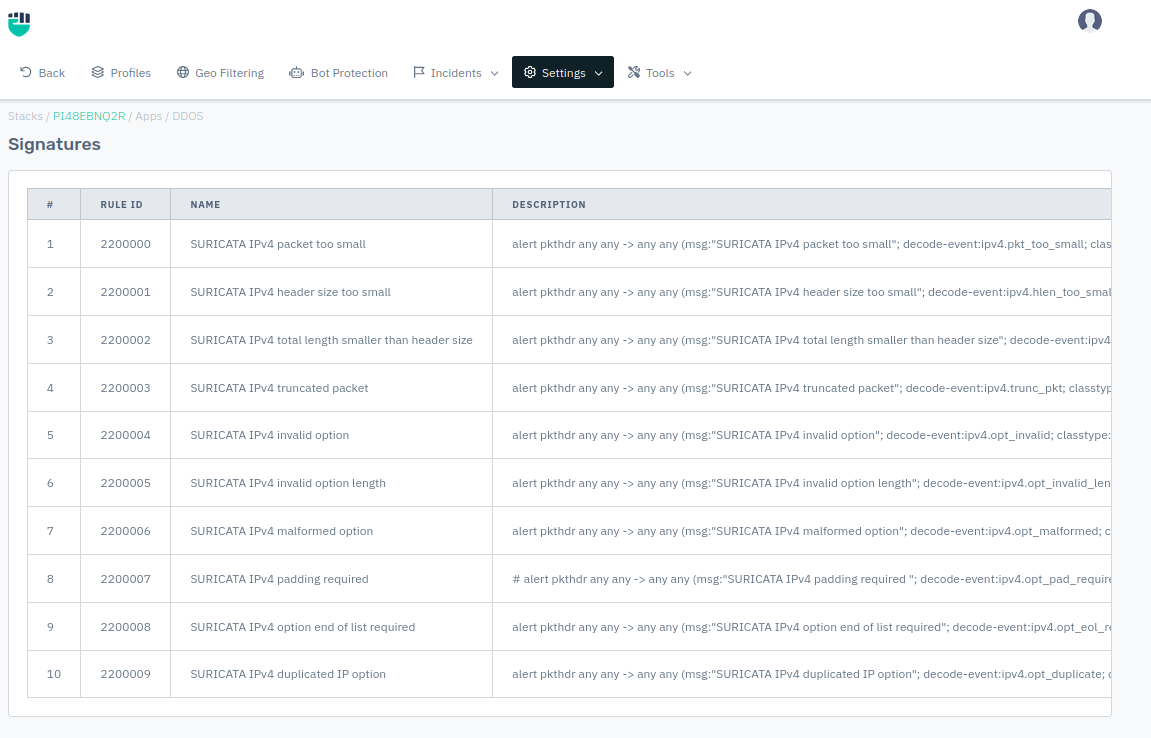
Signatures
Overview
These are in-built rules for DDoS. These are the inbuilt DDoS signatures which help in stopping different types of DDoS Attacks. User can enable/ disable it as per the requirement. These signatures are based on Network IPS/ IDS engines.
How to Use :
- Go to DDoS > Settings > Signatures
- You can change the status of the signature to ENABLED/DISABLED.
- Configurations will be deployed successfully.
Description
Rule ID
Predefined rule ID for the signatures. The ID is unique for each signature.
Name
It specifies the name of the signatures. The name describes the identity of the rule which helps the user understand what is the use of that rule.
Description
It specifies the description of the signature. The name describes the identity of the rule which helps the user understand what is the use of that rule.
Action
It specifies the action need to perform on the current signature rule. In order to delete the rule, we can click on the delete button to remove certain rules in the current security profile. We can also Enable and Disable the signatures.