Overview
Secure your website with Enterprise Grade Web Application Firewall (WAF / WAAP) & Anti-DDoS as a Service
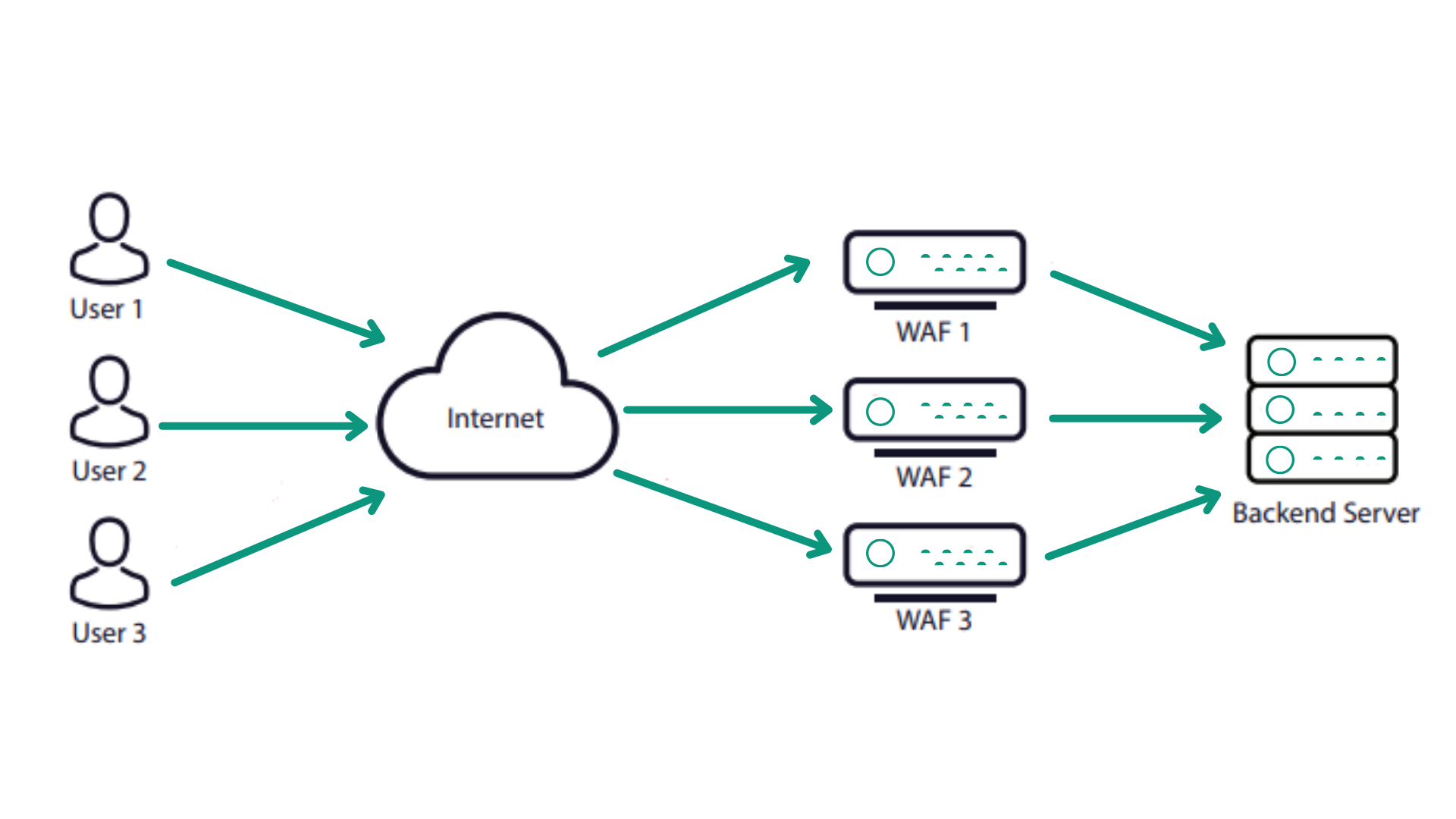
Web Application Firewall (WAF / WAAP) is a reverse proxy solution to secure applications against common cyber-attacks. WAF is designed to protect the company’s Web applications against various critical cyber-attacks such as SQL-Injection, Cross-Site Scripting (XSS), Session Hijacking, and OWASP top 10 vulnerability threats. It sits on an organization’s network, between a Web client and Web server, and protects the organization from vulnerabilities.
Deploying a WAF in front of a web application, a shield is placed between the web client and web server. While a proxy server protects a client machine’s identity by using an intermediary, WAF is a type of reverse proxy, protecting the server from exposure by having clients pass through the WAF before reaching the server.
A WAF operates through a set of rules often called policies. These policies aim to protect against vulnerabilities in the application by filtering out malicious traffic. The value of WAF is the speed and ease with which policy modification can be implemented, allowing for faster response to varying attack vectors. For example, during a DDoS attack, rate limiting can be quickly implemented by modifying WAF policies.
Benefits
Automated Patches
It’s always good to run vulnerability scans regularly. Ideally, if you are in an online business you would be running scans once a quarter or several times a month. Consider what might happen if you discover a vulnerability in your website or application, you might have the resources to patch the application or fix the problem quickly but most businesses don't have the expertise or skill immediately available. If your company falls into the second group, then your company is at risk as long as that vulnerability is present. Haltdos WAFs have the ability to use your scan report to temporarily patch your application for immediate protection.
Stops Data Leakage
Hackers can gather data in numerous ways unless you know you’ve been compromised and detecting them can be challenging. Data leakage can be caused by something as insignificant as a malicious error message presented to a user, so if your application is harboring critical data such as source code or credit card details, then it’s very easy to breach the data and any kind of leak can turn into a disaster. Haltdos WAF scans every response from Web Application to your end-users and if something appears unusual, the WAF stops it from leaving your network. Haltdos WAF has built-in high-level behavioral signatures looking for sensitive information such as credit card details and social security numbers. But you can customize, and add any additional signatures, such as specific files, information, or code.
Rules with Learning
Unlike most WAFs that depend upon attack signatures (aka. rules) to detect and mitigate attacks, Haltdos WAF lookout for new vectors of attacks and continuously publish signatures to mitigate them using a combination of Rules, Artificial Intelligence and Threat Intelligence to provide 360 ° protection for your application. It continuously learns user and application behavior to detect anomalies and take remedial measures to block 0-day attacks.
Positive + Negative Security Model
Haltdos WAF is based on a Negative Security model that protects against known attacks and a Positive Security model that only admits pre-approved traffic. Think of a negative model as a club bouncer instructed to deny admittance to guests who don’t meet the dress code. Now in the positive model, this is like the bouncer at an exclusive party only admits people who are invited. Both negative and positive have their advantages and drawbacks but when combined together with Artificial Intelligence, Haltdos WAF provides comprehensive protection to your website.